Cloud infrastructure consists of servers, storage devices, network, cloud management software, deployment software, and platform virtualization.
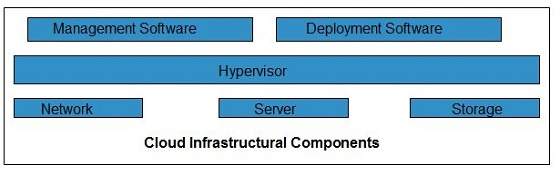
Hypervisor
Hypervisor is a firmware or low-level program that acts as a Virtual Machine Manager. It allows to share the single physical instance of cloud resources between several tenants.
Management Software
It helps to maintain and configure the infrastructure.
Deployment Software
It helps to deploy and integrate the application on the cloud.
Network
It is the key component of cloud infrastructure. It allows to connect cloud services over the Internet. It is also possible to deliver network as a utility over the Internet, which means, the customer can customize the network route and protocol.
Server
The server helps to compute the resource sharing and offers other services such as resource allocation and de-allocation, monitoring the resources, providing security etc.
Storage
Cloud keeps multiple replicas of storage. If one of the storage resources fails, then it can be extracted from another one, which makes cloud computing more reliable.
Infrastructural Constraints
Fundamental constraints that cloud infrastructure should implement are shown in the following diagram:
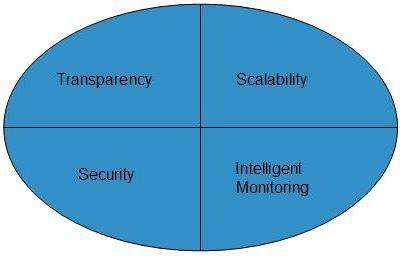
Transparency
Virtualization is the key to share resources in cloud environment. But it is not possible to satisfy the demand with single resource or server. Therefore, there must be transparency in resources, load balancing and application, so that we can scale them on demand.
Scalability
Scaling up an application delivery solution is not that easy as scaling up an application because it involves configuration overhead or even re-architecting the network. So, application delivery solution is need to be scalable which will require the virtual infrastructure such that resource can be provisioned and de-provisioned easily.
Intelligent Monitoring
To achieve transparency and scalability, application solution delivery will need to be capable of intelligent monitoring.
Security
The mega data center in the cloud should be securely architected. Also the control node, an entry point in mega data center, also needs to be secure.
taken from the web tutorialspoint.com may be useful

Post a Comment